Adam and I were virtual participants in NASA’s Space Apps Challenge, a weekend global hackathon the weekend of April 21st encouraging citizen scientists to “solve current challenges relevant to both space exploration and social need”. The event had teams from all 7 continents, including researchers from McMurdo Station, Antarctica, as well as the the International Space Station.
Space Apps Challenge Hackathon
NASA seeded candidate projects prior to the event in 4 categories: software, open hardware, citizen science, and data visualization. Teams could also submit their own proposals. You can view the full list of candidate projects.
I was pleased to see the NASA Planetary Data System (PDS) catalog listed as a seed project. I had looked into programmatically downloading the images available through PDS 6 months ago and discovered that they are stored server-side in the VICAR format, which was unsupported by any open source image processing utilities I could find (ImageMagick nominally has support, but produces garbage images on conversion to other formats). This hackathon was a perfect opportunity to write a utility to convert VICAR into a more accessible format.
vicar2png
Our submission for this hackathon was vicar2png, a utility written in Python with the pypng library to convert VICAR files to the popular PNG image format.
VICAR (the Video Image Communication And Retrieval format), has been used since 1966 for NASA mission images. Check out N1349602309_2.IMG from the Cassini-Huygens mission for an example of a VICAR file. NASA maintains a format specification that we used to implement our solution.
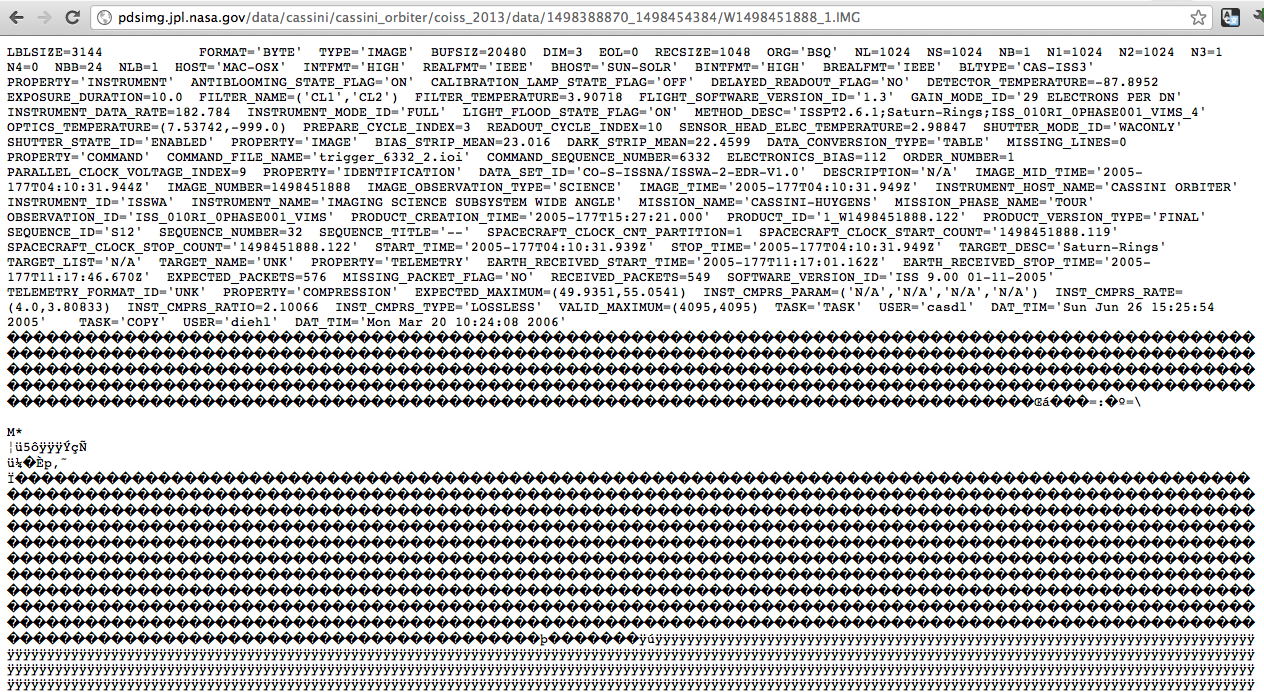
VICAR file from the Cassini-Huygens mission
You can view all of the hackathon submissions.
vicar2png makes it easy for anyone to view, enjoy, and remix NASA’s mission image data easily by converting VICAR files to PNG images. We also hope that making this simple, open source Python implementation available makes it easier for general-purpose open source image processing tools to add VICAR support.
Hackathon deliverables
vicar2png was one of 37 entries nominated for global judging, out of 111 hackathon submissions!

Saturn's moon Phoebe, converted from VICAR data from the Cassini-Huygens mission
Space Apps Challenge Global Judging
For global judging we had to create a short video explaining and demoing our submission.
Global competition deliverables
- Our 3-minute video submission
- The TalentHouse page for our video submission
- I stitched together some short movies using VICAR images from NASA’s Cassini-Huygens mission, for use in our video submission:
Global judging was streamed on uStream; you can view the archived video here. They announced 5 winners:
-
Most Inspiring: Planet Hopper
Visualize exoplanets using Kepler data. -
Best Use of Data:
vicar2png
View, enjoy, and remix NASA’s mission image data easily by converting VICAR files to the popular PNG image format. -
Most Disruptive: Growing Fruits: Pineapple Project
Determine the optimal crop for your community based on rainfall, latitude, elevation, and pH. -
Most Innovative: Strange Desk
Share strange events in your community with other citizen scientists. -
Galactic Impact: Growers Nation
Use location, climate, and growing data to find appropriate crops for unused land. -
“People’s Choice”: Bit Harvester
Control energy systems in remote areas via SMS.
Best use of Data — awesome!
Winners got a miniature spaceship and an interview with Gov 2.0.
We were satisfied to have scoped a hackathon project to meet an actual need we had and could finish in a weekend. Thank you Space Apps Challenge organizers for giving us this opportunity!



Press for global winners
- Our interview with Gov 2.0 Radio (see the full list of Gov 2.0 interviews here)
- A NASA write-up on the Space Apps Challenge winners
Future work
We’d like to use vicar2png as a reference implementation for fixing VICAR support in ImageMagick and adding VICAR support to other open source image processing utilities.
Additionally, NASA uses several other obscure image formats for some of its mission data. In particular, a lot of the Mars Rover images are in the “PDS” image format. As with VICAR, we’d like to write a PDS converter as a step towards increasing the accessibility of the Mars Rover data and to facilitate adding PDS support to other image processing tools.

